内容纲要
概要描述
本文主要介绍,在guardian 3.2.x 版本中,如何在guardian元数据库中,读取某个租户的权限信息。
注意!这篇KB没有考虑 组从角色继承的权限、以及 角色从组继承的权限 这两种复杂场景,如存在,还需额外补充sql逻辑。
详细说明
这里以inceptor组件举例,大致的查询逻辑如下:
非继承权限:
select t1.username,t6.service_name,t7.field_type,t7.field_value,t5.path,t4.action
from gs_user t1
join gs_user_perm t2 on t1.user_id=t2.user_id
join gs_perm t4 on t2.perm_id=t4.perm_id
join gs_resources t5 on t4.resource_id=t5.resource_id
join gs_resource_services t6 on t5.service_id=t6.service_id
join gs_resource_nodes t7 on t5.resource_id=t7.resource_id
where t1.username='lkw'
AND t6.service_name='inceptor1'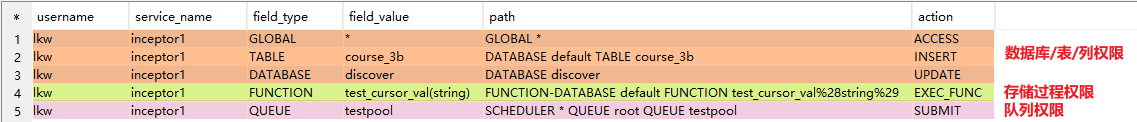
数据库/表/列权限:
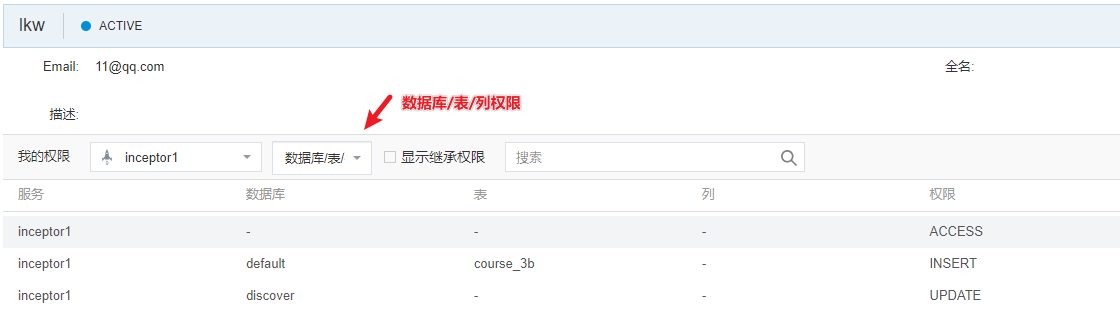
存储过程权限:
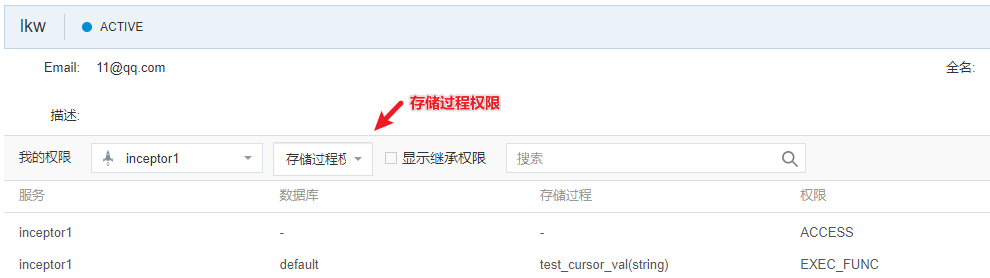
队列权限:
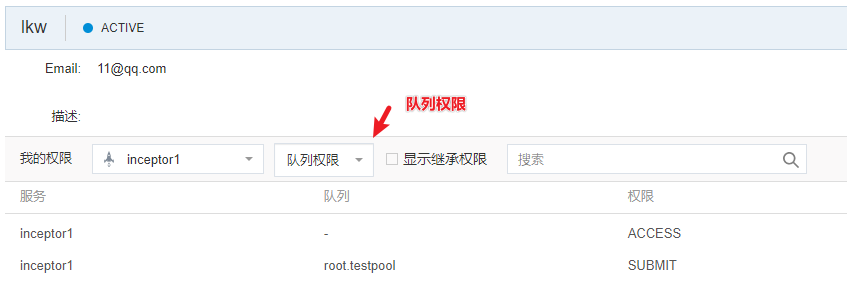
继承权限(From Role):
--sql
select t1.username,t6.service_name,t7.field_type,t7.field_value,t5.path,t4.action
from gs_user t1
join gs_user_role t2 on t1.user_id=t2.user_id
join gs_role_perm t3 on t2.role_id=t2.role_id
join gs_perm t4 on t3.perm_id=t4.perm_id
join gs_resources t5 on t4.resource_id=t5.resource_id
join gs_resource_services t6 on t5.service_id=t6.service_id
join gs_resource_nodes t7 on t5.resource_id=t7.resource_id
where t1.username='lkw'
AND t6.service_name='inceptor1';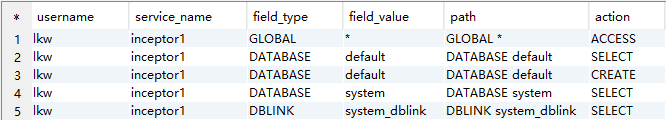
点击租户右下角的角色,进入角色的权限信息页面:
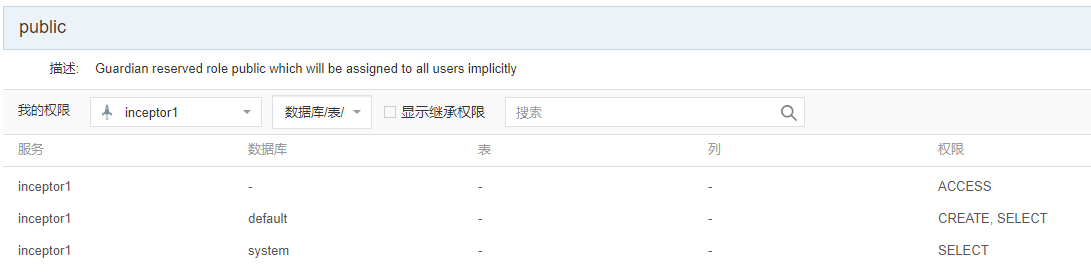
注:这里只选取数据库/表/列权限的样例供参考;另外,guardian 3.2开始不存在角色继承角色的场景,所以这里无需考虑role的多层继承关系。
继承权限(From Group):
这里我们构造一个场景,lkw这个租户归属于组testgroup,而testgroup的父组为FatherGroup。
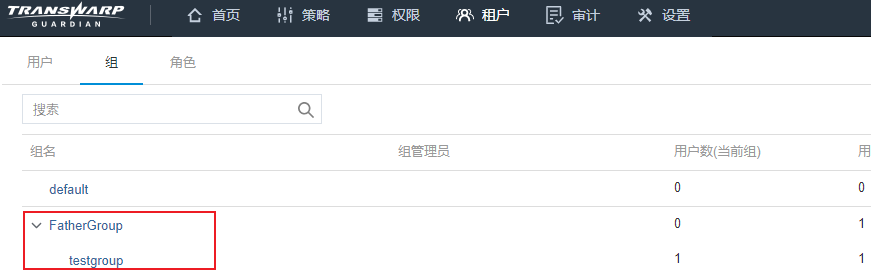
组testgroup,包含了如下权限:
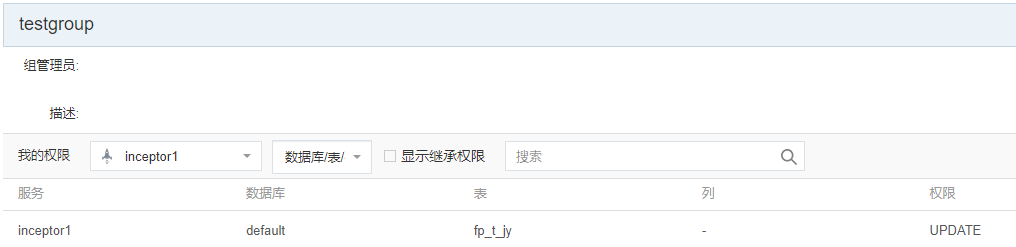
组FatherGroup,包含了如下权:
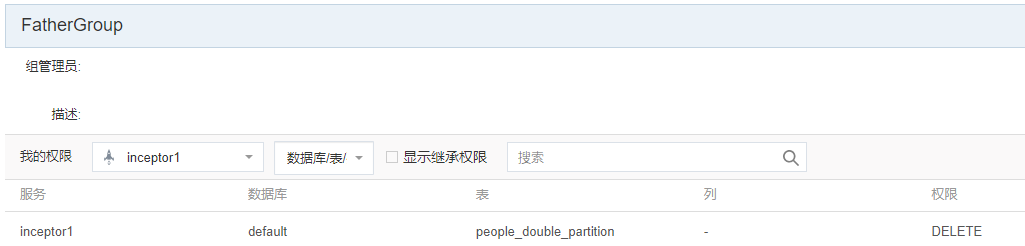
--sql
select t1.username,t6.service_name,t7.field_type,t7.field_value,t5.path,t4.action
from gs_user t1
join gs_user_group t2 on t1.user_id=t2.user_id
join gs_group_perm t3 on t2.group_id=t2.group_id
join gs_perm t4 on t3.perm_id=t4.perm_id
join gs_resources t5 on t4.resource_id=t5.resource_id
join gs_resource_services t6 on t5.service_id=t6.service_id
join gs_resource_nodes t7 on t5.resource_id=t7.resource_id
where t1.username='lkw'
AND t6.service_name='inceptor1';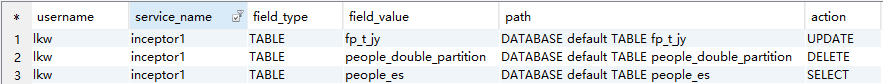
注:这里只选取数据库/表/列权限的样例供参考;另外,Group组的继承,父组层数没有做限制,但是建议不要超过3层。以免有性能问题。
最终,该租户完整的权限信息,union起来是这样:
--非继承权限
select t1.username,t6.service_name,t7.field_type,t7.field_value,t5.path,t4.action
from gs_user t1
join gs_user_perm t2 on t1.user_id=t2.user_id
join gs_perm t4 on t2.perm_id=t4.perm_id
join gs_resources t5 on t4.resource_id=t5.resource_id
join gs_resource_services t6 on t5.service_id=t6.service_id
join gs_resource_nodes t7 on t5.resource_id=t7.resource_id
where t1.username='lkw'
AND t6.service_name='inceptor1';
union
--继承权限(From Role)
select t1.username,t6.service_name,t7.field_type,t7.field_value,t5.path,t4.action
from gs_user t1
join gs_user_role t2 on t1.user_id=t2.user_id
join gs_role_perm t3 on t2.role_id=t2.role_id
join gs_perm t4 on t3.perm_id=t4.perm_id
join gs_resources t5 on t4.resource_id=t5.resource_id
join gs_resource_services t6 on t5.service_id=t6.service_id
join gs_resource_nodes t7 on t5.resource_id=t7.resource_id
where t1.username='lkw'
AND t6.service_name='inceptor1';
union
--继承权限(From Group)
select t1.username,t6.service_name,t7.field_type,t7.field_value,t5.path,t4.action
from gs_user t1
join gs_user_group t2 on t1.user_id=t2.user_id
join gs_group_perm t3 on t2.group_id=t2.group_id
join gs_perm t4 on t3.perm_id=t4.perm_id
join gs_resources t5 on t4.resource_id=t5.resource_id
join gs_resource_services t6 on t5.service_id=t6.service_id
join gs_resource_nodes t7 on t5.resource_id=t7.resource_id
where t1.username='lkw'
AND t6.service_name='inceptor1';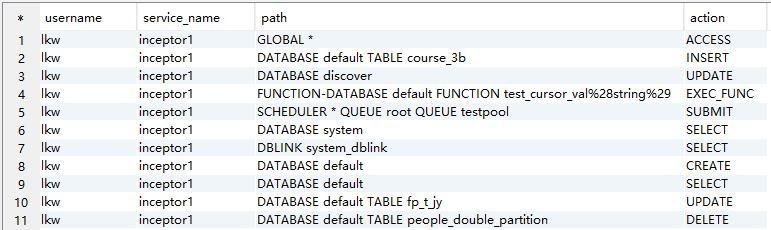
拓展
1.查询所有组件的权限信息
select t1.username,t6.service_name,t7.field_type,t7.field_value,t5.path,t4.action
from gs_user t1
join gs_user_perm t2 on t1.user_id=t2.user_id
join gs_perm t4 on t2.perm_id=t4.perm_id
join gs_resources t5 on t4.resource_id=t5.resource_id
join gs_resource_services t6 on t5.service_id=t6.service_id
join gs_resource_nodes t7 on t5.resource_id=t7.resource_id
where t1.username='lkw'
union
select t1.username,t6.service_name,t7.field_type,t7.field_value,t5.path,t4.action
from gs_user t1
join gs_user_role t2 on t1.user_id=t2.user_id
join gs_role_perm t3 on t2.role_id=t2.role_id
join gs_perm t4 on t3.perm_id=t4.perm_id
join gs_resources t5 on t4.resource_id=t5.resource_id
join gs_resource_services t6 on t5.service_id=t6.service_id
join gs_resource_nodes t7 on t5.resource_id=t7.resource_id
where t1.username='lkw'
union
select t1.username,t6.service_name,t7.field_type,t7.field_value,t5.path,t4.action
from gs_user t1
join gs_user_group t2 on t1.user_id=t2.user_id
join gs_group_perm t3 on t2.group_id=t2.group_id
join gs_perm t4 on t3.perm_id=t4.perm_id
join gs_resources t5 on t4.resource_id=t5.resource_id
join gs_resource_services t6 on t5.service_id=t6.service_id
join gs_resource_nodes t7 on t5.resource_id=t7.resource_id
where t1.username='lkw'
order by 2,3 asc;2. 获取哪些用户对某张表具有查询权限:
需要考虑如下几个方面
field_type='TABLE'表级的SELECT和ADMIN权限field_type='DATABASE'数据库级的SELECT和ADMIN权限field_type='GLOBAL'全局级的SELECT和ADMIN权限
比如,我现在想查看对default库下people_es表的查询权限;
select username,service_name,field_type,field_value,path,action from
(select t1.username,t6.service_name,t7.field_type,t7.field_value,t5.path,t4.action
from gs_user t1
join gs_user_group t2 on t1.user_id=t2.user_id
join gs_group_perm t3 on t2.group_id=t2.group_id
join gs_perm t4 on t3.perm_id=t4.perm_id
join gs_resources t5 on t4.resource_id=t5.resource_id
join gs_resource_services t6 on t5.service_id=t6.service_id
join gs_resource_nodes t7 on t5.resource_id=t7.resource_id
UNION
select t1.username,t6.service_name,t7.field_type,t7.field_value,t5.path,t4.action
from gs_user t1
join gs_user_role t2 on t1.user_id=t2.user_id
join gs_role_perm t3 on t2.role_id=t2.role_id
join gs_perm t4 on t3.perm_id=t4.perm_id
join gs_resources t5 on t4.resource_id=t5.resource_id
join gs_resource_services t6 on t5.service_id=t6.service_id
join gs_resource_nodes t7 on t5.resource_id=t7.resource_id
UNION
select t1.username,t6.service_name,t7.field_type,t7.field_value,t5.path,t4.action
from gs_user t1
join gs_user_group t2 on t1.user_id=t2.user_id
join gs_group_perm t3 on t2.group_id=t2.group_id
join gs_perm t4 on t3.perm_id=t4.perm_id
join gs_resources t5 on t4.resource_id=t5.resource_id
join gs_resource_services t6 on t5.service_id=t6.service_id
join gs_resource_nodes t7 on t5.resource_id=t7.resource_id) tb
where
service_name='inceptor1'
and ((field_type='TABLE' AND field_value='people_es' AND ACTION IN ('ADMIN','SELECT'))
or (field_type='DATABASE' AND field_value='default' AND ACTION IN ('ADMIN','SELECT'))
or (field_type='GLOBAL' AND field_value='*' AND ACTION IN ('ADMIN','SELECT')))
order by 1,5;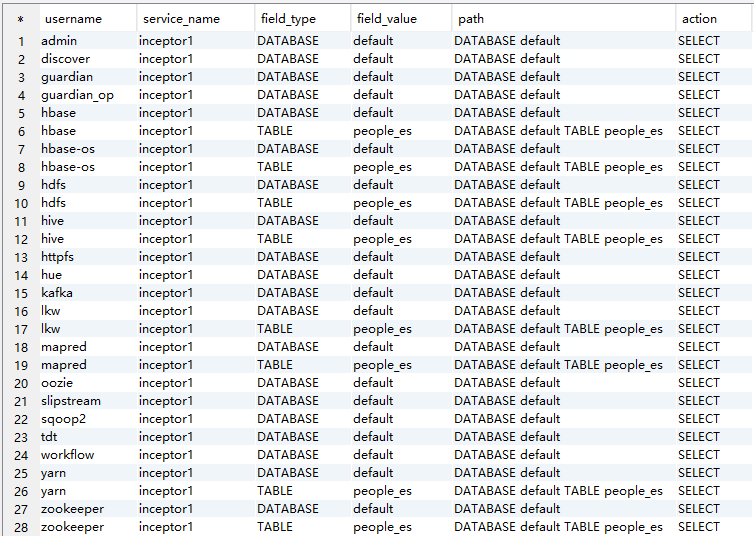
FAQ
1. 多个inceptor共享metastore的情况下,权限是共享的(除了队列权限)
如果多个inceptor组件,共享了metastore,那么说明元数据也是共享的,同个用户对同一份数据的权限必然是相同的。
共享metastore的情况独享的只是计算资源,比如队列的权限就是独享的。
所以在使用上面语句的时候需要检查inceptor组件是否存在共享metastore的情况。