概要描述
星环科技TOS组件中的节点通信由证书控制, 其中一个控制服务端通信的证书会在2023-03-10日过期。
证书过期后将可能会影响集群的正常使用。
详细说明
续签主要有以下几个步骤:
- 确认证书是否需要续签
- 下载证书包
- 备份原证书
- 续签证书
- 复制证书至所有 etcd 节点以及 其他 节点
- 重启 etcd、apiserver 服务生效
- 修改 tos 模板文件,确保 Manager 可以将证书分发到其他所有节点
- 更新 Manager 数据库中的历史证书数据
证书续签过程有任何问题,都可以通过恢复第3步备份的原证书,然后从第4步重新开始,不会对集群有破坏性影响。
1、确认受影响的版本
如下版本将会受到影响:
- TDH:
- 受影响的TOS版本:1.9.x ≤ TOS版本 ≤ 2.1.x
- TDH 5.x 之后的版本,请检查是否受到影响
- TDC:
- 受影响的TOS版本:1.9.x ≤ TOS版本 ≤ 2.0.x
- TDC 2.4 之前的所有版本(TDC版本 < 2.4)
为了保证集群的健康运行,请在证书过期前(2023-03-10)更新证书。
您可以进入到集群 Manager /srv/kubernetes/ 目录下,使用下面两个命令查看过期时间:
# openssl x509 -text -in /srv/kubernetes/etcd-ca.pem | grep "Not"
Not Before: Mar 11 10:30:00 2018 GMT
Not After : Mar 10 10:30:00 2023 GMT
# kubectl version
Client Version: version.Info{Major:"2", Minor:"1+", GitVersion:"v2.1.0-tos-final-build-20220805-tdh", GitCommit:"c413e8244dbf13e8726be0751fdc3f870d7888cd", GitTreeState:"clean", BuildDate:"2022-08-05T13:37:59Z", GoVersion:"go1.12.10", Compiler:"gc", Platform:"linux/amd64"}
Server Version: version.Info{Major:"2", Minor:"1+", GitVersion:"v2.1.0-tos-final-build-20220805-tdh", GitCommit:"c413e8244dbf13e8726be0751fdc3f870d7888cd", GitTreeState:"clean", BuildDate:"2022-08-05T13:37:59Z", GoVersion:"go1.12.10", Compiler:"gc", Platform:"linux/amd64"}
本文主要介绍通过纯手工方式续签证书
若您的环境可以使用脚本的方式,您可以参考 TOS etcd-ca 及相关证书脚本化续签 使用脚本方式更新证书。
本文测试使用节点:
172.22.25.10 jiujiu-tdh-10
172.22.25.11 jiujiu-tdh-11
172.22.25.12 jiujiu-tdh-122、下载证书包及manager数据库更新脚本
默认环境部署完成 etcd-ca.key会不存在,需要从安装包拷贝或者从本文下载 ,
X86 环境证书包下载:
点击下载gencerts目录文件
arm-64环境证书包下载:
点击下载arm64 环境gencerts目录
manager数据库更新脚本下载:
点击下载 更新manager数据库脚本
将下载的 gencerts 上传到第一台 tos master/etcd 节点上,然后直接解压即可(tar -zxvf gencerts.tar.gz)。
将下载的update_manager_info.sh(数据库更新脚本) 放到manager节点
后续续签及生成证书的操作默认都在第一台 tos master/etcd 节点。
3、备份节点上原有证书目录
所有 tos-master 节点执行
# cp -r /srv/kubernetes /srv/kubernetes-bak4、续签证书
4.1 依赖于原 etcd-ca.pem 和 etcd-ca-key.pem 生成 etcd-ca-new.pem
[root@jiujiu-tdh-11 ~]# cd gencerts
[root@jiujiu-tdh-11 gencerts]# openssl x509 -in etcd-ca.pem -days 36500 -out etcd-ca-new.pem -signkey etcd-ca-key.pem
Getting Private key4.2 查看新 etcd-ca 证书过期时间
[root@jiujiu-tdh-11 gencerts]# openssl x509 -text -in etcd-ca-new.pem | grep "Not"
Not Before: Jan 10 10:01:32 2023 GMT
Not After : Dec 17 10:01:32 2122 GMT4.3 使用任一个依赖于 etcd-ca.pem 生成的证书进行证书比对,这边使用的是 etcd.pem
[root@jiujiu-tdh-11 gencerts]# openssl verify -CAfile etcd-ca-new.pem /srv/kubernetes/etcd.pem
/srv/kubernetes/etcd.pem: OK到此 etcd-ca.pem 证书续期完毕
4.4 获取etcd节点和scv的ip
以下etcd节点ip为172.22.25.10,172.22.25.11,172.22.25.12,
hostname为jiujiu-tdh-10,jiujiu-tdh-11,jiujiu-tdh-12
对于已经过期的集群的节点获取方式:
[root@jiujiu-tdh-10 ~]# openssl x509 -in /srv/kubernetes/etcd.pem -noout -text |grep -i dns
DNS:jiujiu-tdh-10, DNS:jiujiu-tdh-11, DNS:jiujiu-tdh-12, IP Address:127.0.0.1, IP Address:10.10.10.1, IP Address:172.22.25.10, IP Address:172.22.25.11, IP Address:172.22.25.12[root@jiujiu-tdh-10 ~]# kubectl get po -owide -n kube-system |grep etcd
tos-etcd-tos-jiujiu-tdh-10 1/1 Running 0 1d 172.22.25.10 jiujiu-tdh-10
tos-etcd-tos-jiujiu-tdh-11 1/1 Running 0 1d 172.22.25.11 jiujiu-tdh-11
tos-etcd-tos-jiujiu-tdh-12 1/1 Running 0 1d 172.22.25.12 jiujiu-tdh-12以下 svc的ip为10.10.10.1
[root@jiujiu-tdh-10 ~]# kubectl get svc
NAME TYPE
kubernetes ClusterIP 10.10.10.1 443/TCP 1y 4.5 重新生成 etcd 相关证书:etcd.csr、etcd-key.pem、etcd.pem
需要将命令中-hostname后面hostname和ip改成当前操作集群的etcd节点的(获取方法如4.4,hostname以命令获取的为准),并且加上svc的ip和127.0.0.1
127.0.0.1为必写固定的,10.10.10.1为上面步骤2.1获取的svc的ip,cfssl和cfssljson均在gencerts目录下
如下:
[root@jiujiu-tdh-11 gencerts]# ./cfssl gencert -ca=etcd-ca.pem -ca-key=etcd-ca-key.pem -config=config.json -profile=etcd -hostname=jiujiu-tdh-10,jiujiu-tdh-11,jiujiu-tdh-12,127.0.0.1,10.10.10.1,172.22.25.10,172.22.25.11,172.22.25.12 kubernetes-csr.json | ./cfssljson -bare etcd
2023/01/10 18:37:52 [INFO] generate received request
2023/01/10 18:37:52 [INFO] received CSR
2023/01/10 18:37:52 [INFO] generating key: rsa-2048
2023/01/10 18:37:53 [INFO] encoded CSR
2023/01/10 18:37:53 [INFO] signed certificate with serial number 5049842162445944011430072579403750159527881611425、 拷贝新证书到本节点的/srv/kubernetes/和其他master节点以及Manager节点
5.1. 复制到本节点的/srv/kubenetes下
[root@jiujiu-tdh-11 gencerts]# cp etcd-ca-new.pem /srv/kubernetes/etcd-ca.pem
[root@jiujiu-tdh-11 gencerts]#
[root@jiujiu-tdh-11 gencerts]# cp etcd.pem etcd-key.pem /srv/kubernetes/
cp:是否覆盖"/srv/kubernetes/etcd.pem"? y
cp:是否覆盖"/srv/kubernetes/etcd-key.pem"? y5.2. scp到集群中的其他所有节点(tos-master 以及 Manager节点)
[root@jiujiu-tdh-11 gencerts]# cd /srv/kubernetes
[root@jiujiu-tdh-11 kubernetes]# scp etcd-ca.pem etcd.pem etcd-key.pem root@172.22.25.10:/srv/kubernetes/
root@172.22.25.10's password:
etcd-ca.pem 100% 2082 745.5KB/s 00:00
etcd.pem 100% 1870 3.3MB/s 00:00
etcd-key.pem 100% 1675 2.8MB/s 00:00[root@jiujiu-tdh-11 kubernetes]# scp etcd-ca.pem etcd.pem etcd-key.pem root@172.22.25.12:/srv/kubernetes/
root@172.22.25.12's password:
etcd-ca.pem 100% 2082 904.1KB/s 00:00
etcd.pem 100% 1870 41.7KB/s 00:00
etcd-key.pem 100% 1675 3.5MB/s 00:005.3. scp到集群中的flannel服务的所有安装节点上(TDC不影响,未安装flannel的节点不影响,不影响的集群可不操作)
若安装了flannel服务,需要将其复制到flannel的所有安装节点上
- 获取flannel所在节点,如下显示flannel节点为jiujiu-tdh-10, jiujiu-tdh-11, jiujiu-tdh-12,与etcd节点重合, 故不需要做额外的复制操作
[root@jiujiu-tdh-10 ~]# kubectl get po -owide -n kube-system |grep flannel flanneld-flannel-kg54q 1/1 Running 1 94d 172.22.25.11 jiujiu-tdh-11 flanneld-flannel-xcsq5 1/1 Running 0 3d 172.22.25.12 jiujiu-tdh-12 flanneld-flannel-z5rv7 1/1 Running 2 152d 172.22.25.10 jiujiu-tdh-10 kube-dns-flannel-768v7 1/1 Running 0 3d 172.22.25.12 jiujiu-tdh-12 kube-dns-flannel-c6888 1/1 Running 3 94d 172.22.25.11 jiujiu-tdh-11 kube-dns-flannel-nxdxv 1/1 Running 2 152d 172.22.25.10 jiujiu-tdh-102.若flannel所在节点为非etcd/tos master节点 则需要将更新了的证书复制到这些节点
# scp /srv/kubernetes/etcd* root@《非etcd节点的ip》:/srv/kubernetes/
6、 重启相关服务
6.1 检查etcd服务状态(若不正常请联系星环售后技术支持)
将下面命令中的jiujiu-tdh-10,jiujiu-tdh-11,jiujiu-tdh-12修改成步骤 4.4 获取的 etcd 的 hostname
[root@jiujiu-tdh-11 ~]# ETCDCTL_API=3 etcdctl --cacert /srv/kubernetes/etcd-ca.pem --cert /srv/kubernetes/etcd.pem --key /srv/kubernetes/etcd-key.pem --endpoints https://jiujiu-tdh-10:4001,https://jiujiu-tdh-11:4001,https://jiujiu-tdh-12:4001 endpoint status
2023-01-12 19:29:33.107430 I | warning: ignoring ServerName for user-provided CA for backwards compatibility is deprecated
https://jiujiu-tdh-10:4001, 58b07431c59f5a61, 3.1.18, 15 MB, false, 386, 14180208
https://jiujiu-tdh-11:4001, ca5c6c5dcde5192e, 3.1.18, 15 MB, true, 386, 14180208
https://jiujiu-tdh-12:4001, e6f4c353dbabdd8d, 3.1.18, 15 MB, false, 386, 14180208
# etcd 是一主两备,有一个 true 和 2个 false 是正常状态
[root@jiujiu-tdh-11 ~]# ETCDCTL_API=3 etcdctl --cacert /srv/kubernetes/etcd-ca.pem --cert /srv/kubernetes/etcd.pem --key /srv/kubernetes/etcd-key.pem --endpoints https://jiujiu-tdh-10:4001,https://jiujiu-tdh-11:4001,https://jiujiu-tdh-12:4001 endpoint health
2023-02-15 16:40:05.373542 I | warning: ignoring ServerName for user-provided CA for backwards compatibility is deprecated
2023-02-15 16:40:05.374429 I | warning: ignoring ServerName for user-provided CA for backwards compatibility is deprecated
2023-02-15 16:40:05.375645 I | warning: ignoring ServerName for user-provided CA for backwards compatibility is deprecated
https://jiujiu-tdh-11:4001 is healthy: successfully committed proposal: took = 2.288165ms
https://jiujiu-tdh-12:4001 is healthy: successfully committed proposal: took = 9.113096ms
https://jiujiu-tdh-10:4001 is healthy: successfully committed proposal: took = 16.162234ms
6.2 所有etcd节点上依次重启etcd和apiserver
在其他 etcd 节点也要顺序执行以下同样的操作
1.停止 etcd 和 apiserver
[root@jiujiu-tdh-11 gencerts]# mv /opt/kubernetes/manifests-multi/tos-etcd.manifest /opt/kubernetes/[root@jiujiu-tdh-11 gencerts]# mv /opt/kubernetes/manifests-multi/tos-apiserver.manifest /opt/kubernetes/2.确认 container 不存在后,等待30s,继续后面步骤
[root@jiujiu-tdh-11 gencerts]# docker ps |grep tos-etcd
[root@jiujiu-tdh-11 gencerts]# [root@jiujiu-tdh-11 gencerts]# docker ps |grep apiserver
[root@jiujiu-tdh-11 gencerts]#3.启动 etcd 和 apiserver
[root@jiujiu-tdh-11 gencerts]# mv /opt/kubernetes/tos-etcd.manifest /opt/kubernetes/manifests-multi/[root@jiujiu-tdh-11 gencerts]# mv /opt/kubernetes/tos-apiserver.manifest /opt/kubernetes/manifests-multi/在其他 etcd 节点也按照顺序执行以上操作之后
- 检查 etcd 节点状态是否正常
[root@jiujiu-tdh-11 ~]# ETCDCTL_API=3 etcdctl --cacert /srv/kubernetes/etcd-ca.pem --cert /srv/kubernetes/etcd.pem --key /srv/kubernetes/etcd-key.pem --endpoints https://jiujiu-tdh-10:4001,https://jiujiu-tdh-11:4001,https://jiujiu-tdh-12:4001 endpoint status
2023-01-12 19:29:33.107430 I | warning: ignoring ServerName for user-provided CA for backwards compatibility is deprecated
https://jiujiu-tdh-10:4001, 58b07431c59f5a61, 3.1.18, 15 MB, false, 386, 14180208
https://jiujiu-tdh-11:4001, ca5c6c5dcde5192e, 3.1.18, 15 MB, true, 386, 14180208
https://jiujiu-tdh-12:4001, e6f4c353dbabdd8d, 3.1.18, 15 MB, false, 386, 14180208
# etcd 是一主两备,有一个 true 和 2个 false 是正常状态
[root@jiujiu-tdh-11 ~]# ETCDCTL_API=3 etcdctl --cacert /srv/kubernetes/etcd-ca.pem --cert /srv/kubernetes/etcd.pem --key /srv/kubernetes/etcd-key.pem --endpoints https://jiujiu-tdh-10:4001,https://jiujiu-tdh-11:4001,https://jiujiu-tdh-12:4001 endpoint health
2023-02-15 16:40:05.373542 I | warning: ignoring ServerName for user-provided CA for backwards compatibility is deprecated
2023-02-15 16:40:05.374429 I | warning: ignoring ServerName for user-provided CA for backwards compatibility is deprecated
2023-02-15 16:40:05.375645 I | warning: ignoring ServerName for user-provided CA for backwards compatibility is deprecated
https://jiujiu-tdh-11:4001 is healthy: successfully committed proposal: took = 2.288165ms
https://jiujiu-tdh-12:4001 is healthy: successfully committed proposal: took = 9.113096ms
https://jiujiu-tdh-10:4001 is healthy: successfully committed proposal: took = 16.162234ms
- 确保 apiserver 的container 正常运行
[root@jiujiu-tdh-11 gencerts]# docker ps -a |grep apiserver
38ca327d181e 46ad5fa4c35f "hyperkube apiserver…" 3 seconds ago Up 1 second k8s_tos-apiserver-tos_tos-apiserver-tos-jiujiu-tdh-11_kube-system_e6a3c26e60fad7c80fea893016c4a9e8_0
70a3ada56731 transwarp/pause:manager-7.0.1910a-final "/pause" 3 seconds ago Up 2 seconds k8s_POD_tos-apiserver-tos-jiujiu-tdh-11_kube-system_e6a3c26e60fad7c80fea893016c4a9e8_0
[root@jiujiu-tdh-11 gencerts]#
6.3 重启flannel服务
kubectl delete po $(kubectl get po -owide -n kube-system |grep flannel|awk '{print $1}') -n kube-system7. 更新metainfo目录下的证书和manager数据库
manager-6.0.1811a之后的版本会存储tos证书到数据库中分发到各个节点,同时生成其他证书相关的逻辑会使用metainfo中的etcd-ca.pem,所以需要更新相关文件和数据库数据,防止后续角色重启变更分发证书导致证书再次失效
7.1 更新metainfo目录下证书
- 找到当前tos版本的对应的metainfo目录
在任意节点使用root 执行 :kubectl describe po $(kubectl get pods -n kube-system |grep registry|awk '{print $1}') -n kube-system |grep -i image:可获取tag
例1:
[root@jiujiu-tdh-12 ~]# kubectl describe po $(kubectl get pods -n kube-system |grep registry|awk '{print $1}') -n kube-system |grep -i image:
Image: transwarp/registry:manager-7.0.1910a-final
Image: transwarp/registryui:manager-7.0.1910a-final对应的在manager 节点的tos 目录应该是 /var/lib/transwarp-manager/master/content/meta/services/TOS/manager-7.0.1910a-final/templates/gencerts/
例2:
[root@argodb1~]$ kubectl describe po $(kubectl get pods -n kube-system |grep registry|awk '{print $1}') -n kube-system |grep -i image:
Image: transwarp/registry:tos-2.1对应的在manager 节点的tos 目录应该是 /var/lib/transwarp-manager/master/content/meta/services/TOS/tos-2.1/templates/gencerts/
注意!manager节点不一定是tos master/etcd 节点,请根据实际情况从已经更新过证书的节点拷贝到manager节点
- 将上面新生成的etcd-ca.pem证书替换到对应的/var/lib/transwarp-manager/master/connent/meta/services/TOS/tos版本/templates/gencerts/目录下(etcd.pem和etcd-key.pem会在manager分发证书的时候重新执行生成命令)
[root@jiujiu-tdh-10 ~]# cd /srv/kubernetes
## manager-7.0.1910a-final为 上一步骤获取的版本
[root@jiujiu-tdh-10 gencerts]# cp etcd-ca.pem /var/lib/transwarp-manager/master/content/meta/services/TOS/manager-7.0.1910a-final/templates/gencerts/- 将/var/lib/transwarp-manager/master/content/meta/services/TOS/tos版本/templates/gencerts/目录下的config.json文件中的expiry 的87600h改为 876000h
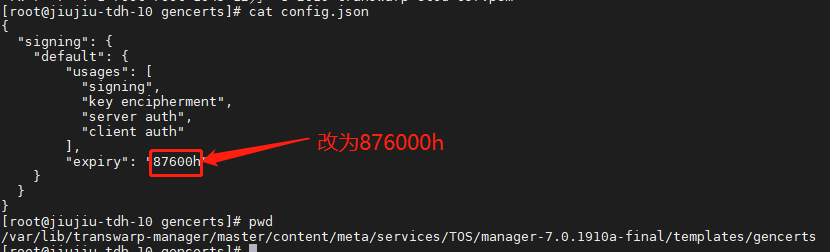
8 更新Manager 中历史证书数据(脚本和手动的方式二选一)
8.1 脚本操作
使用 上面 步骤2 下载的更新manager数据库的脚本更新
- 将update_manager_info.sh 脚本放到manager节点上
- 赋权并执行脚本
chmod +x update_manager_info.sh ./update_manager_info.sh
8.2 手动操作
8.2.1. 备份原表
根据 各个版本查看Manager后台数据的方法 进入Manager数据库
create table manager_info_bak2023 like manager_info;
insert into manager_info_bak2023 select * from manager_info;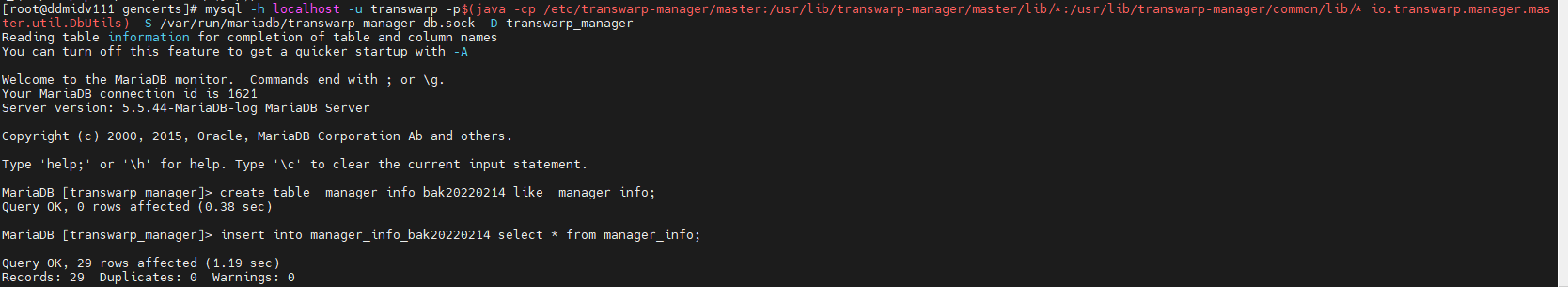
8.2.2. 更新证书数据:
1.在manager节点执行下面命令获取刚刚更新的证书内容
cat /srv/kubernetes/etcd-ca.pem
cat /srv/kubernetes/etcd-key.pem
cat /srv/kubernetes/etcd.pem2.根据 manager数据库进入方法 进入manager数据库,执行下面sql
证书内容为上一步获取的
update manager_info set value="etcd-ca.pem证书内容" where key="etcd-ca.pem";
update manager_info set value="etcd.pem证书内容" where key="etcd.pem";
update manager_info set value="etcd-key.pem证书内容" where key="etcd-key.pem";注意!证书内容要全部复制到, 后面不要有多余的回车
例如:
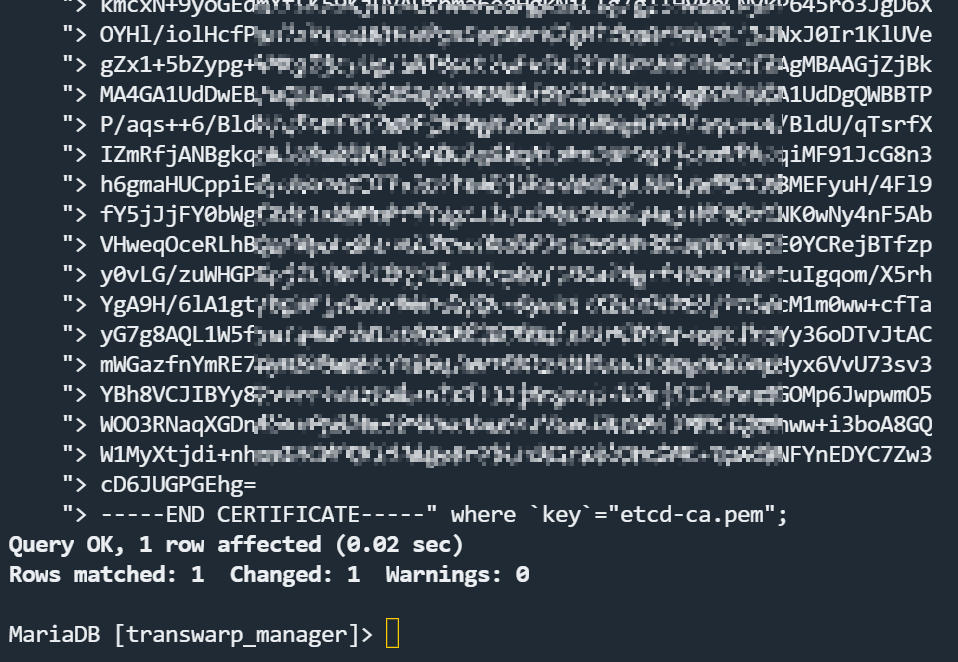
9、确认证书替换成功,过期时间已经如期延长
更新过的证书验证方法
openssl x509 -text -in /srv/kubernetes/etcd-ca.pem | grep "Not"
openssl x509 -text -in /srv/kubernetes/etcd.pem | grep "Not"
## tos版本在步骤4.1获取
openssl x509 -text -in /var/lib/transwarp-manager/master/content/meta/services/TOS/tos版本/templates/gencerts/etcd-ca.pem | grep "Not"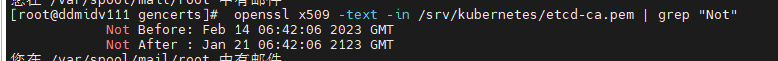
若有任何疑问, 请及时咨询 星环科技售后技术支持